Catalogues

NVR4208-8P-I AI network video recorder
375x 321 x 53.8 mm(1 U), 8 channel IP video access, up to 2 channel video stream face recognition/ 8 channel picture stream face recognition, support 10 face databased with total 20,000 face images, H.265+ H.264 format, provide 2 SATA III ports, up to 8TB capacity for each HDD, 8 POE ports
Download Specification
OverviewSpecificationApplicationsSupport
NVR4208-8P-I is an AI NVR that integrated advanced AI technology, which provides high precision human face recognition and perimeter protection. It is compatible with numerous third-party devices, which make it the perfect solutions for surveillance systems.
Face recognition, face match Video
System Topology I
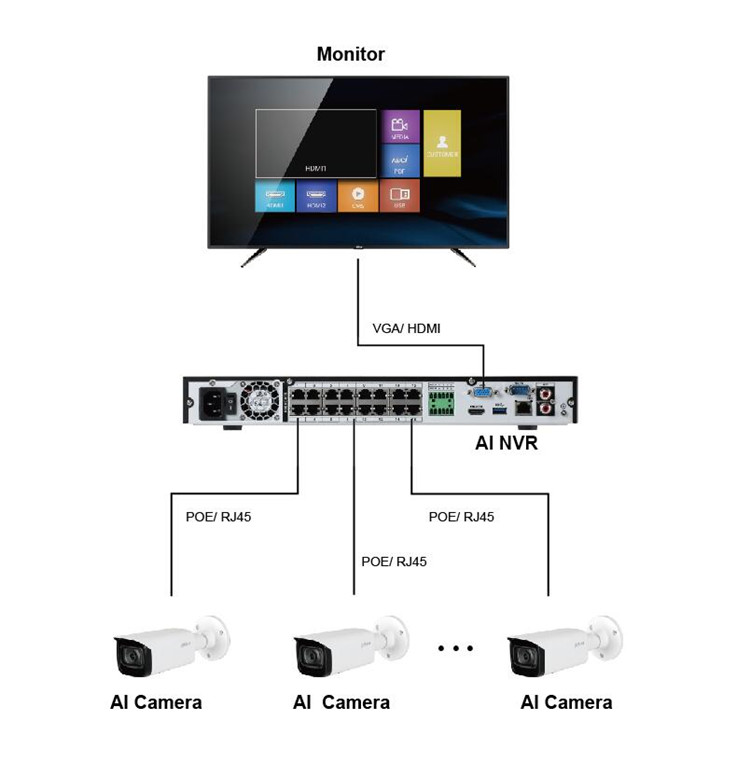
Main features:
• 8 Channel IP video access
• H.265 & H.264 triple stream encoding
• Up to 4 channel perimeter protection
• Up to 8 channel picture stream face recogonition/ Up to 2 channel video stream face recognition
• Up to 12 face pictures/ sec processing speed
• Up to 10 face databases with 20,000 face images management in total, support add name, gender, birthday, address, certificate, certificate No, countries properties to each face image
• Common mode & Stranger mode, in stranger mode, when detected a stranger, NVR will trigger alarm, buzzer, snapshot, record, etc.
• Automatic number plate recognition available for parking lot managements, support license plate recognition, black/ white list import/ export, search result ( working with ITC camera)
|
System
|
|
| Main Processor | Multi-core embedded processor |
| Operating System | Embedded LINUX |
| Perimeter Protection | |
| Performance | 4 channel, 10 IVS rules for each channel |
| Object classification | Human/Vehicle secondary recognition for tripwire and intrusion |
| AI Search | Search by target classification (Human, Vehicle) by targe |
| Face Recognition | |
| Performance | Max 12 face pictures /sec processing |
| 2 channel video stream face recognition / 8 channel picture stream face recognition ( with FD camera) | |
| Stranger Mode | Detect strangers' faces(not in device's face database).Similarity threshold can be set manually. |
| AI Search | Up to 8 target face images search at same time, similarity threshold can be set for each target face image. |
| Database Management | Up to 10 face databases with 20,000 face images in total. Name, gender, birthday, address, certificate type, certificate No., countries®ions and state can be added to each face picture. |
| Database Application | Each database can be applied to video channels independently. |
| Trigger Events | Buzzer, Voice Prompts, Email, Snapshot, Recording, Alarm Out, PTZ Activation, etc. |
| Audio and Video | |
| IP Camera Input | 8 Channel |
| Two-way Talk | 1 Channel Input, 1 Channel Output, RCA |
| Display | |
| Interface | 1 HDMI, 1 VGA |
| Resolution | HDMI/VGA: 3840 x 2160, 1920 × 1080 , 1280 × 1024, 1280 × 720 , 1024 × 768 |
| Decoding Capability | 2-ch@8MP(30fps), 8-ch@1080P(30fps) |
| Multi-screen Display | 1/4/8/9 |
| Recording | |
| Bandwidth | 200Mbps (80Mbps when AI function enabled, based on private protocol) |
| Compression | Smart H.265+/H.265/Smart H.264+/H.264/MJPEG |
| Resolution | 12MP, 8MP, 6MP, 5MP, 4MP, 3MP, 1080P, 1.3MP, 720P, D1 etc. |
| Record Mode | Manual, Schedule (Continuous, MD(Motion Detection) , Alarm, IVS) |
| Record Interval | 1 ~ 120 min (default: 60 min), Pre-record: 1 ~ 30 sec, Post-record: 10 ~ 300 sec |
|
Video Detection and Alarm
|
|
| Trigger Events | Alarm Out, Video Push, Email, Recording, PTZ, Tour, Snapshot, Voice Prompt, Buzzer and Screen Tips |
| Video Detection | Motion Detection, MD Zones: 396 (22 × 18), Video Loss, Tampering and Scene Change |
| Alarm Input | 4 Channel |
| Alarm Output | 2 Channel |
| Playback and Backup | |
| Sync Playback | 36990 |
| Search Mode | Time /Date, Alarm, MD and Exact Search (accurate to second) |
| Backup Mode | USB Device/Network |
| Third-party Support | |
| Third-party Support | Arecont Vision, Airlive, AXIS, Canon, Dynacolor, JVC, LG, Panasonic, Pelco, Xunmei, Samsung, Sanyo, Sony, Watchnet and more |
| Network | |
| Interface | 1 RJ-45 Port (10/100/1000Mbps) |
| PoE | 8 ports (IEEE802.3af/at) |
| 1-8 ports support ePoE & EoC | |
| Network Function | HTTP, HTTPS, TCP/IP, IPv4/IPv6, UPnP, SNMP, RTSP, UDP, SMTP, NTP, DHCP, DNS, IP Filter, PPPoE,DDNS, FTP, Alarm Center, IP Search (Support) |
| IP camera, DVR, NVS, etc.), P2P | |
| Max. User Access | 128 users |
| Mobile App | iPhone, iPad, Android |
| Interoperability | ONVIF (Profile S), SDK, CGI |
| Storage | |
| Internal HDD | 2 SATA III Ports, Up to 8 TB capacity for each HDD |
| eSATA | NA |
| Auxiliary Interface | |

In transportation and ticketing feild, the traditional payment is by a simple paper ticket that bears some of security features, like florescent ink, security line, latent image, barcode, infra-red ink. Through it can be prevent most of the fake tickets, however hard work load, low identification rate, and relevant unsafe features enforce institutions had to recruit abundant workforce to maintain normally operation, and now everything was changed as RFID technology deeply implanted into this sector.
At most of bus station or subway station, you will not no longer find any paper tickets any more, which replaced them was a simple recharge card or NFC mobile phones. And in recent years, the pace of changing speeds up dramatically.
Thanks to the RFID technology, you do need to wait in line for ticket checking, all just by a simple touch, and you are allowed to get through, and payment will automatically deducted by the RFID readers.
The benefits are not only in its convenience, but also its security. Each RFID card will have a unique ID, which is permanently stored in its ROM, and can not be rewritten. Meanwhile the communication between the RFID card and RFID readers is encrypted. Let’s take oyster card( London metro card) for example, this type of card is embedded with NXP Mifare Desfire chip, which the chip is integrated with the 3DES encryption technology, and still now there is zero case of password being cracked.
This RFID technology also have been applied into certain of big event, such as Olympics, World Expo…
In the future, we will see more and more case of this advanced RFID technology being applied in our normal life, and therefore change our life for ever.

It is not a new story that RFID applied into the access control sector. The earliest RFID technology that emerged in Access control setor shall turn back time to mid 20th century, And it was first introduced at low frequency of 125 khz, with a unique ID number inside the chip. EM4100 chip, as one of the most typical chips, emerged in this stage. It brought a hurricane to the traditional access control sector, which the traditional physical keys were gradually replaced by a piece of card. It not only brings convenience but also maintain high security.
Glory of ATT5557 chips in access control system
While as technology developed, the traditional EM4100 chip is no longer worked well, because the ID number could be easily duplicated, which make its safety severely be doubted. Then ATA5557 chips emerged in the stage, it is a chip with pin code embedded, which allow user to set up the password for safety concerns. To better protect the password, this T5557 chip also adopt a interesting settings, which if the password misread for over 3 times, the chip will permanently locked and can not be used any more. The market’s response is so appreciated that access control systems based on T5557 chips rapidly occupy the market.
Lord of chips for NXP Mifare 1k s50 chips
Time turns to 21st century, NXP mifare 1k chips, which worked at high frequency of 13.56 Mhz whipped up a thunderstorm. It was no longer merely bear UID code or passwords, it extended the multiple functions, up to 1kB memory organized in 16 independent sectors, each sectors could sets an application and its passwords. It is amazing function, which make multiple applications in one card possible, beside it contains a logical counter, which allows it able to conduct plus and deduct algorisms. It was so popular as if all the RFID cards bear this Mifare 1k chip in one night. It is still the most welcome chip in the market.
New Emperor- NFC mobile phones and bio technology in access control
Early at year 2005, Nokia have published its NFC mobile phone, which could conduct the same functions as Mifare 1k s50 chip does. This emerged NFC technology though is fantastic, it is not accepted by user’s then. In 2007, Apple launched innovative Iphone, which completely overturn the whole phone sector. And this impact also affect the newly born NFC technology, the Andriod Mobile phone is the first mobile that publicly support NFC technology. By using this technology, NFC that used in Access control is gradually into reality.
Advantages of RFID in access control
Contactless identification with limited read distance. Just a simply touch will the card be indentified. Limited read range also provide user protecting their user’s data and prevent unwanted operation
Access control data management. RFID technology help users more efficiently manage visitor’s access data, such as vistor’s profile, password and access authority through relevant RFID software. Time attendance system is based on this idea.
Security . RFID provides reliable security features either by its unique ID and password or by its encryption algorisms. Especially when advanced DES and 3DES encryption algorisms introduced, user data by nowadays technology is impossible to break.
Related Products
-
IPC-HFW5241T-SE AI Camera >

1/2.8" 2 M pixel CMOS, 25/ 30 fps @1080P ( 1920 x 1080), H.265 & H.264, face detection

 RF Identification
RF Identification Optical Identification
Optical Identification Biometric Identification
Biometric Identification Transportation & Ticketing
Transportation & Ticketing Access control
Access control Health & Medicine
Health & Medicine Food & Wine
Food & Wine Apps for NFC mobile
Apps for NFC mobile Manuals
Manuals Software
Software FAQ
FAQ Service Center
Service Center Company news
Company news Industry news
Industry news Technical communication
Technical communication


